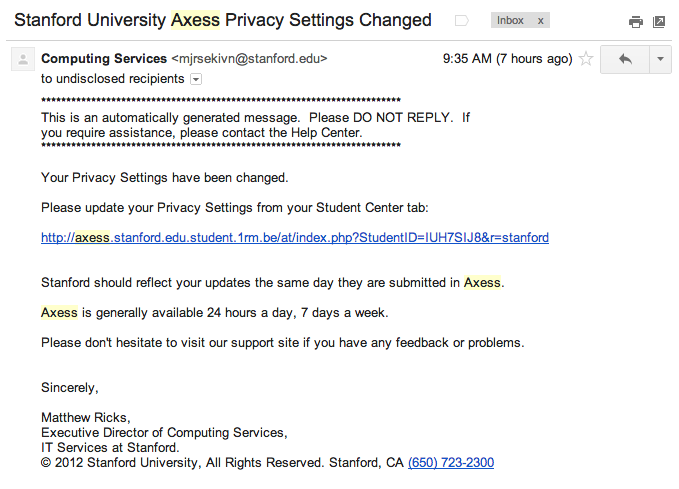
A new email phishing attack has recently targeted “several thousand” members of the Stanford community, according to University administrators and residential computer consultants (RCCs).
“This is one of the cleverest scams IT services has seen yet,” wrote Kathy Fisher, administrative associate in the Department of Developmental Biology, in an email to a departmental mailing list.
The email, which was sent from a series of email addresses ending in “@stanford.edu” and falsely signed by Executive Director of Computing Services Matthew Ricks, claims that the recipient’s privacy settings have been changed in Axess. Through offering a fake link to Axess, the scam aims to trick recipients into submitting login information into what appears to be a Stanford WebLogin page.
“[The email] is NOT an official email communication from Stanford University,” wrote Registrar Tom Black in an email to students. “It is a phishing attempt to capture your SUNet ID and password.”
Black advised students who submitted information through the email’s fake link to change their SUNet ID password.
Though the phishing email was sent from a series of random addresses in the “@stanford.edu” domain, Sherwin Smith, Residential Computing consulting services manager, emphasized that the scam was externally launched and highlighted its complexity.
“It is easy to make something look like it came from an address,” Smith said. “Phishing attacks are extremely common. … Usually they are not as well crafted as this one, which may be why it was as significant an attempt.”
According to Suites RCC Will Dannemann ’14, victims of the phishing attack could also potentially have other online accounts compromised through the use of the same password.
“If one gets compromised, the other gets compromised,” Dannemann said. “A lot of these attacks are based on going after a relatively low-priority password, and assuming people use the same password for different account.”
Dannemann advised students to take precautionary measures to minimize the risk of falling victim to phishing attacks in the future.
“The most effective thing to do is to keep different passwords for different accounts, use two-step authorization [and] don’t click on suspicious-looking email links,” Dannemann said.
In addition to offering similar guidance to students and community members, the University also subscribes to a filtering service intended to screen phishing attacks and spam before they reach their intended recipients.
“This type of attack is fairly common and we filter out the vast majority of these types of messages,” wrote Nancy Ware, director of strategic planning and communications for IT Services, in a statement. “This message was very targeted at Stanford and thus was not initially picked up by the filter. We updated our filters to block this once it started being delivered.”
While the University is currently attempting to identify the message’s sender, new instances of the phishing email were still being reported by students as of Monday afternoon. Several thousand email addresses across campus have received the message, but the number of recipients who clicked on the link is unknown, according to Ware.
“If a student receives an email that they’re not sure is legitimate or not, assume it’s not,” Smith recommended. “They can always hit up their RCC and have them take a look at it.”