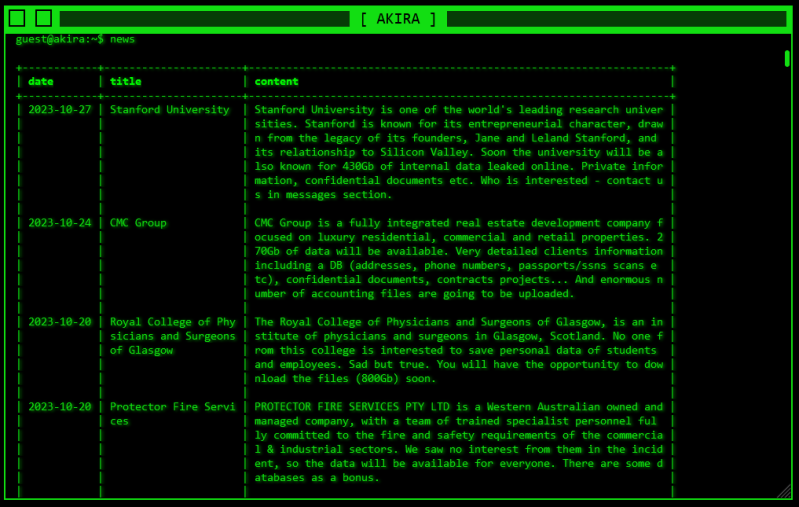
Notorious ransomware gang ‘Akira’ listed Stanford University on the darknet as the target of a ransomware attack on Friday morning. Screenshots of the listing were shared on other parts of the internet, including the r/stanford subreddit and on X (formerly Twitter) by cyber risk analyst Brett Callow.
University spokesperson Luisa Rapport confirmed “this is the same as the SUDPS cybersecurity incident” previously covered by The Daily.
Akira claims to hold 430 gigabytes of internal data, including private information and confidential documents. They threatened to leak the information online if the University did not pay an unspecified ransom. The Stanford University Department of Public Safety processes and stores data on personnel, case reports, risk evaluations and crime involving students, faculty and other community members. It is unclear at this point how much of this data was lost or encrypted by this ransomware.
The University wrote in a Friday statement that “there is no indication that the incident affected any other part of the university, nor did it impact police response to emergencies.” According to the statement, “the investigation is ongoing and once it is completed, we will act accordingly and be able to share more information with the community.”
The Akira listing describes Stanford as “known for its entrepreneurial character.” The group threatened that, “Soon the university will be also known for 430Gb of internal data leaked online. Private information [and] confidential documents.”
Chris Hoofnagle, law professor and director of the Center for Law & Technology at the University of California, Berkeley, wrote to The Daily that attackers interested in police entities are sometimes “a nation state or organized crime” group.
“The first steps of identifying the scope of the breach can be quite expensive and time consuming. Almost all entities hire outside forensic firms to do the analysis,” Hoofnagle wrote.
He wrote it was “best practice” to limit information until there was information on the full scope of the breach and the network was secure. “Institutions do not want to get into a drip situation where they notify people of a breach, then later learn the breach was worse than understood, and then have to give more and more notices,” Hoofnagle wrote.
Following the listing, Hoofnagle wrote that, “Stanford could pay the ransom — many companies do.” He advised students to file a security alert if they were concerned personal data was exposed.
Akira refers to a family of ransomware, first identified in March 2023, that is tied to several dozen attacks across organizations in the U.S. and Canada. The group’s operations are consistent: demanding ransom payments ranging from $200,000 to $4 million, and publishing data online if payment is not fulfilled.
The darknet website also serves as a hub of all former leaks and news about upcoming leaks. Data from previous victims is accessible via magnet links which anonymously connect you with other users on the network, who share the file directly. Akira listed more than 60 organizations since March, including U.S. energy company BHI and Mercer University in Georgia.
Cybersecurity firms like Avast and Arctic Wolf identified meaningful connections between Akira and Conti, another ransomware first observed in 2020 and believed to be distributed by a Russia-based group. Investigations revealed that breached entities received the following message:
“Whatever who you are and what your title is if you’re reading this it means the internal infrastructure of your company is fully or partially dead, all your backups – virtual, physical – everything that we managed to reach – are completely removed. Moreover, we have taken a great amount of your corporate data prior to encryption.”
According to University spokesperson Dee Mostofi, the investigation is still very active. The University’s “privacy and information security teams have been giving this matter their concerted attention, in coordination with outside specialists,” Mostofi wrote.
The Palo Alto Daily Post reported on potential liabilities Saturday. Cybersecurity expert Ahmed Banafa told the Daily Post that “someone could sue Stanford if they have sealed arrest records or body camera footage that gets leaked. There’s a lot of important and famous and important people at Stanford who might not want to be exposed.”
Noah Abrahamson, director of cloud security and information security office operations, confirmed in response to concerns shared on the University IT Slack Channel that his team was “aware” of the listing.
SUDPS directed The Daily to the University statement when asked for a comment.
The Daily reached out to Akira representatives for comment on the scope and legitimacy of the listing through an anonymous portal.